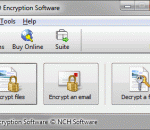
MEO is a free data encryption application (for non-commercial use). This powerful tool can encrypt or decrypt files of any type, including Microsoft Word, Excel and PDF documents. MEO allows you to protect your sensitive data against un-authorized viewers by utilizing the latest data encryption technologies. Keep your documents safe and secure with this free data encryption software.
Privacy Eraser is an all-in-one privacy suite that protects your privacy by cleaning up all your Internet history tracks and past computer activities. It supports popular web browsers such as Internet Explorer, Mozilla Firefox, Google Chrome, Safari and Opera, completely implements and exceeds the US Department of Defense and NSA clearing and sanitizing standard, once erased with it, your file data is gone forever and can not be recovered.
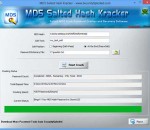
Salted MD5 Hash Password Cracker and Recovery Software
Child Lock is a handy, easy to use tool specially designed to help you lock the keyboard and mouse so that they aren't available for kids. Can be set to autolock after a period of inactivity - stops little fingers once you have left the PC. Can block out windows control keys - switch out of the current application (provided the app is running fullscreen such as a game).
RogueKiller x64 offers multilingual support, uses low CPU and RAM, and carries out a scan job rapidly. We have not come across any issues throughout our evaluation, as the app did not hang or crash. Although it is not particularly intuitive or attractive, RogueKiller x64 proves to be a pretty powerful tool for detecting and removing suspicious activity from the system.
The True Key app protects your passwords by scrambling them with AES-256, one of the strongest encryption algorithms available. Only you can decrypt and access your information with the factors you choose. Intel Security respects your privacy. Your passwords belong only to you — accessible only by you. We never share or sell your data.
Audit and recovery of Cassandra passwords. Account information import from databases. Password recovery using dictionary attacks, brute force attacks, hybrid dictionary/brute force attacks. Generation of reports on recovered passwords.
Hide Folders is an innovative software application which enables you to password protect all the private information on your hard drive. You can swiftly make your files and folders inaccessible, invisible or protect them from modification or removal. The protected folders or files are not accessible by users - no matter how they are trying to get in - locally or from the net.
Help prevent online bullying and cyber-grooming Know if your child is a victim of cyber bullying or grooming. AVG Family Safety® uses key-stroke technology to monitor your child's activities in chat-rooms and on social networking sites. If it spots words, phrases or language that are known to be used to victimize children online, it will notify you immediately via SMS or email.
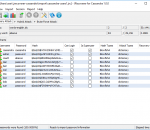
TinyWall includes a combination of features that sets it apart from both commercial and freeware firewalls. TinyWall does not display popups that "urge users to allow". In fact, it will not notify you of any blocked action. Rather than displaying popups, TinyWall allows users to whitelist or unblock programs via various methods.
G-Zapper helps you stay anonymous while searching Google by blocking and deleting the Google search cookie. Did you know that Google stores a unique identifier in a cookie on your PC, which allows them to track the keywords you search for? G-Zapper helps you protect your identity and search history by allowing you to view your Google ID, see how long your searches have been tracked, erase your searches, and block the Google search cookie.