Shared Folder Protctor is designed for for corporate usage, help you to protect sharing files on Lan and on removable device. Users can browser the documents but not able to copy and modify them that lets you prevent illegal copying of your files.With Shared Folder Protctor, organizations can defend their intellectual property, customer and partner data and corporate brand equity.
CrococryptMirror is an encryption tool which mirrors complete folders to encrypted folders. The encryption algorithms that are used are AES and Twofish (256 bits, cascading). The keyfile is secured by a password using PKCS #5 (PBKDF2) with a SHA512/Whirlpool based HMAC using 100000 iterations and also AES and Twofish. Mirroring can be done manually (on-demand) or by using the sync service which detects directory changes on the fly.
NeoGuardian allows management to monitor how work time is spent, both on and offline. It reports on websites visited, activity on each website and length of time each application is open and running for. Websites can be blocked specifically by employers, or alternatively allowed during break times and not work hours through scheduling.
EventSentry is the proactive, real-time monitoring solution that watches over your servers, workstations and network devices to ensure maximum availability and that also helps with SOX, HIPAA and other compliance requirements. With EventSentry you can consolidate and monitor event logs and log files in real-time as well as monitor performance, disk space, services, processes and software/hardware installations on servers and workstations.
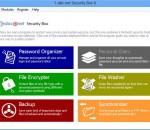
There are many programs to protect your privacy and system security, but this easy-to-use collection combines 6 fantastic modules to improve your data security and will guide you step by step on your way to a safer system! Including Password Organizer, Personal Diary, File Encrypter, File Washer, Backup and Synchronizer. This suite protects your personal data, encrypts or wipes files and saves your important files scheduled and automatically!
Cryptic Disk creates virtual encrypted disks and also encrypts hard disks, USB drives and memory cards. This allows you to maintain secrets both on a home computer and on a workstation. Data encryption makes use of the best algorithms (any of the following modern cryptographic algorithms can be used: AES/Rijndael, Serpent, Twofish, Blowfish, CAST6), and takes place in real time without affecting computer performance. Cryptic Disk provides its use
Send e-mail messages easily and securely from your portable PC while you are traveling around the world! Using this program instead of your ISP's SMTP server you will increase your e-mail security and privacy as well as get rid of annoying change of settings for your e-mail program. Easy SMTP Server is easy to configure!
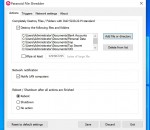
Paranoid File Shredder securily shreds all your secret files across LAN computers. You can trigger shredding by launching special program, using hotkey or receiving notification from LAN. Triggering shredding action on one computer can make other computers start shredding.
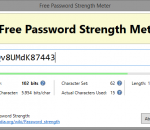
Free Password Strength Meter checks the level of strength of your passwords. It uses information entropy as a measure of strength and reliability. It shows you the level of password strength using a scale of levels: very weak, weak, reasonable, good, strong and very strong. It is recommended to use only strong and very strong passwords. Check your passwords and use only strong and secure passwords to protect your privacy.
OutlookPasswordDecryptor is the FREE tool to instantly recover forgotten password for all versions of Outlook Application.
BSNL Modem/Router Password Recovery Software